The Tor (The Onion Route) browser makes anonymous browsing of the Internet possible. The incognito or the privacy mode feature available in various browsers is not the same as anonymity. Typically, people use the Tor browser to keep their internet activities private from websites and advertisers, and to evade censorship in certain parts of the world. Although, users in countries with heavy censorship can’t even download Tor and software products alike. The reason I say typically, because this anonymity, of course can be used for criminal and malicious purposes as well. Business executives, IT professionals and law enforcement officers also use Tor to mask their IP addresses when working undercover, or needing to investigate dubious web sites.
First off, cyber-hackers use the power of anonymity to cover their digital tracks. Cyber criminals also use the hidden services, or onion services, to host their websites, which are part of the dark web. These websites are accessible primarily by the Tor browser.
The Tor Project (https://www.torproject.org/) was launched in 2002 with an emphasis on protecting the digital privacy of the users.
A few words of caution.
- Do not use the Tor browser while other browsers are open in the background.
- Do not download anything from the dark web if you managed to reach those hidden websites with Tor mainly because you don’t know what you’re downloading.
- If you find a document or material that you must download for whatever reason, shut down all browsers before opening the downloaded material.
- This is simply because the downloaded material can reveal your digital identity to the site where it came from. Of course, if the material is an infected program or malware, then it won’t matter whether the browser is open or not!
Now, back to the subject of anonymity.
Tor encrypts user data and then transfers the data through different relays within the Tor network. This creates a multi-layered encryption and protects the digital identity of the user. It hides the source and the destination of your Internet traffic, preventing spying eyes from knowing who you are and what you are looking at. Electronic Frontier Foundation (https://www.eff.org/pages/tor-and-https) uses a simple animation that shows what information is revealed when using and/or not using the combination of Tor and HTTP/S protocol.
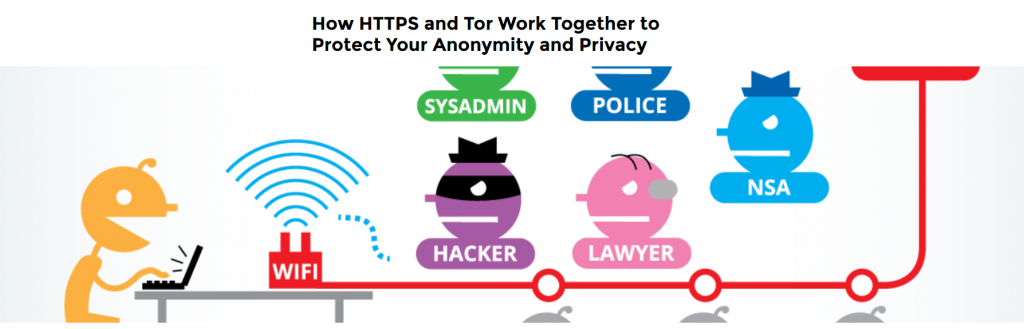
Keep in mind, if you use Tor to access websites that are accessible only within the U.S., you may be denied access to those sites. For instance, if you attempt to reach your bank’s website with Tor, you may be challenged with additional security questions and the wonderful captcha. This is because your bank’s website received a request coming from outside the country.
Another point worth considering is the exit node or the exit relay. As shown in the diagram, you need to exit the Tor network at some point to contact the final destination. If wo/manned by an unscrupulous operator, this exit node can be used to reveal the user’s identity.

If you decide to use Tor, use it for legitimate reasons and be smart about it. To use an analogy, you may know how to use a gun without proper training but you don’t know when it’ll misfire or when you may mishandle it!
-Max